Crypto scams: How to spot fraud and protect your investments

While crypto transaction records are tamper-proof, users are not immune to fraud and scams, ranging from non-existent projects to phishing. Bitcoin’s record price highs — fueled in part by Donald Trump's policies — are attracting even the tech-averse. Profit opportunities are plentiful, but so are the lurking risks. Here's how to spot common red flags.
Growing scale and diversity of scams
Crypto crime costs users billions. In Q1 2025 alone, over $2 billion was lost to hacks, with Bybit's exploit accounting for a staggering $1.4 billion. Meanwhile, scammers stole $96.37 million through phishing and $300 million via rug pulls.
No one is immune — with “even the biggest centralized and decentralized players falling victim to operational failures, access control weaknesses, and, in a few cases, social engineering,” according to a Hacken report.
Top 5 common crypto scams
Phishing attacks
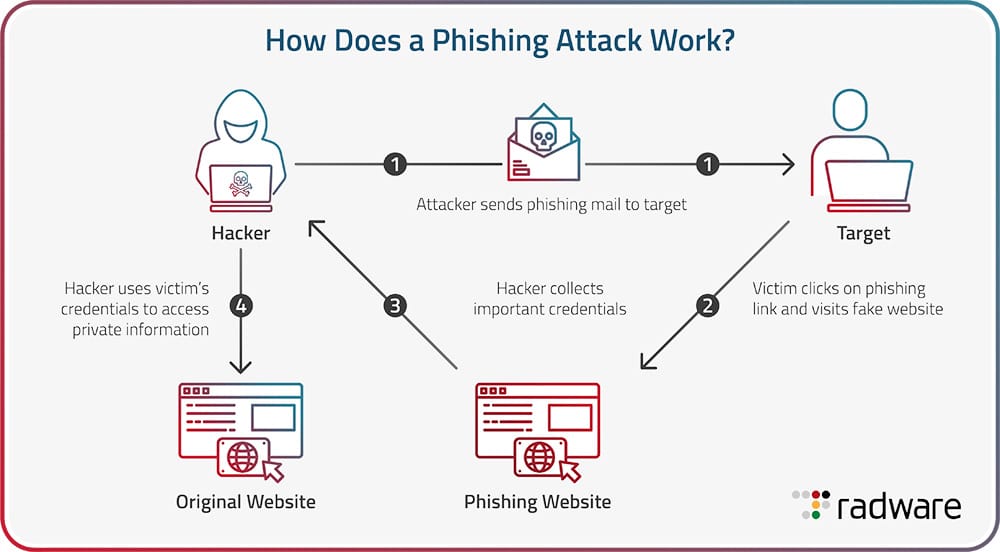
Phishing involves using emails or texts to steal sensitive data like private keys or login details. Scammers impersonate a trusted entity — often popular crypto exchanges — to manipulate users.
The attack starts with a message (typically from a fake email or social media account) containing a link to a fraudulent website disguised as legitimate. If the victim enters their credentials, scammers gain immediate access.
Example
Owners of Ledger wallets have received suspicious emails urging them to upgrade their software. The messages contained a link to a fake Ledger Live application that would trigger a transaction.
Prevention tips
- Never click links without verifying the sender. Even if the message appears to be from a trusted company, confirm it matches their official channels.
- Watch for red flags like spelling, grammar, or awkward language.
- Enable two-factor authentication (2FA) so scammers can’t access your account even with login details.
Ponzi schemes
Ponzi schemes predate cryptocurrency by centuries. They lure investors with promises of outsizedreturns but pay early participants using funds from new victims.
In crypto, they often appear as high-yield investment programs (HYIPs), offering unrealistic passive gains. These scams rely on paid promoters and fake legitimacy before collapsing.
Example
BitPetite posed as a revolutionary platform combining crypto, DeFi, and NFTs. Soon after its ICO, its market cap hit $200 million, despite the absence of a convincing whitepaper or any real underlying technology. The project creators sold off their BPET tokens, the price crashed to zero, and BitPetite vanished into thin air.
Similarly, PlusToken soared to a market cap of over $17 billion before collapsing as one of the largest scams in history. The platform attracted millions of users with high yields via Ponzi-style payouts — until its founders shut down all withdrawals and disappeared with the funds.
Prevention tips
- Be skeptical of "too good to be true" returns.
- Research thoroughly — Ponzi schemes prey on those who skip due diligence.
Fake ICOs
Initial coin offerings (ICOs) are the crypto version of initial public offerings (IPOs) for stocks. Like their TradFi predecessors, ICOs are designed to attract funding for crypto projects through token sales. The ICO model enables scammers to launch fake projects and steal from investors, leaving them with worthless tokens.
Typical red flags resemble those for Ponzi schemes include an absence of a rigorous whitepaper and claims that seem too good to be true. Any suspicious project-related materials should ring alarm bells.
Example
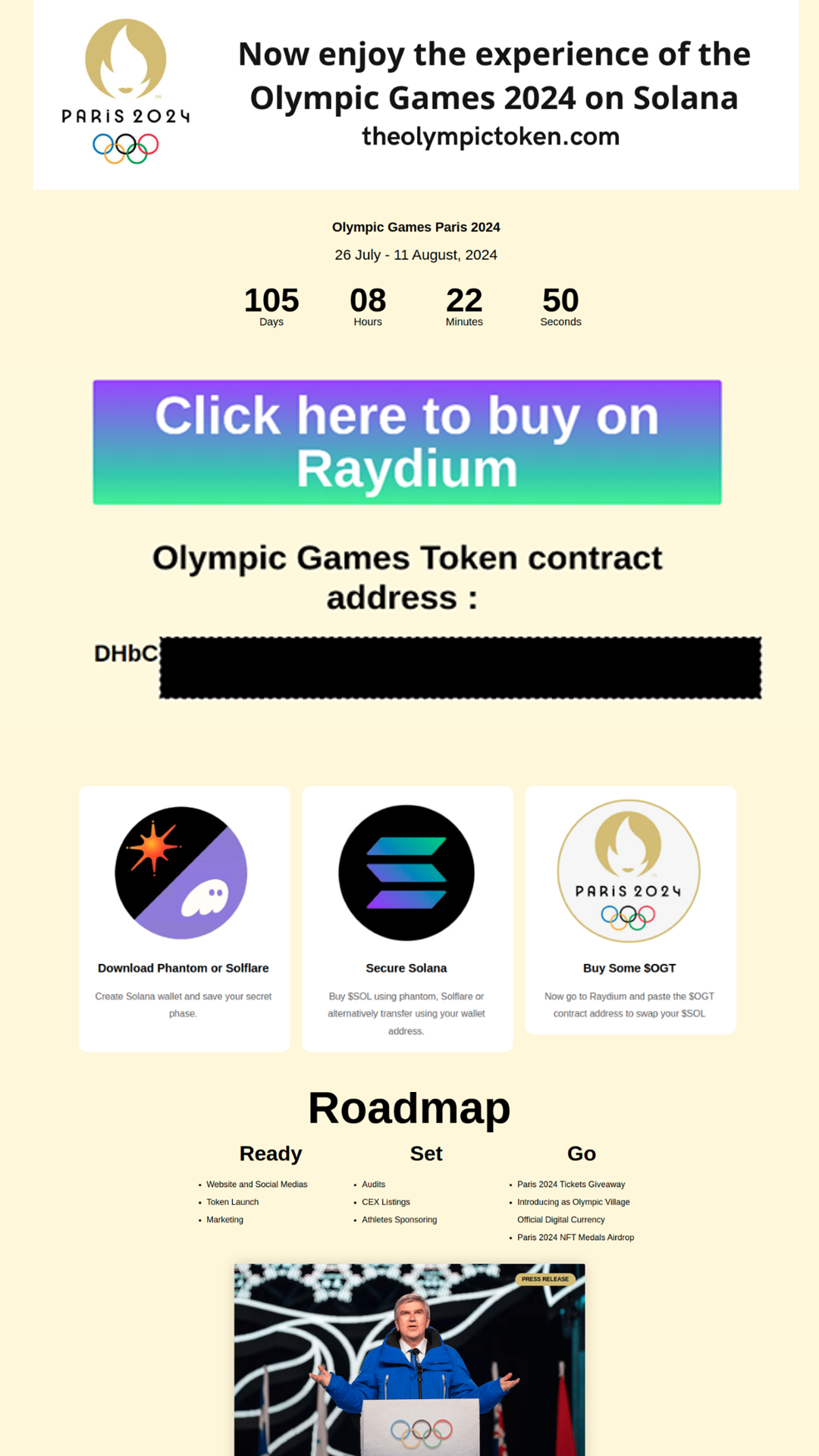
In 2024, crypto ICP scams leveraged the Olympics to lure victims. One such website — theolympictoken.com — featured a vague project roadmap, used the official Olympics logo, and stated it was affiliated to the International Olympic Committee. The whitepaper link led to the legitimate olympics.com website instead of an actual document.
Prevention tips
- Research any ICO thoroughly before investing.
- Use trusted ICO ranking platforms and third-party reviewers to help identify scams and find legitimate projects worth supporting.
Rug pulls
The idiom "pulling the rug out from under someone" describes situations where a victim is left in a compromising position. In crypto, a "rug pull" is an exit scam where developers suddenly drain a project's liquidity or assets post-launch, leaving investors with worthless tokens.
These tokens are aggressively promoted on social media — often using paid crypto influencers. Scammers typically exploit liquidity pools (decentralized crypto reserves that can be traded without an exchange). This approach allows them to bypass standard vetting procedures for exchange listings.
Example
This year, founders of MetaYield Farm — positioned as a DeFi yield farming protocol — disappeared with $290 million secured from over 14,000 investors. Its entire online presence was wiped out, eroding trust in DeFi. Meanwhile, the LIBRA token, promoted by Argentine President Javier Milei, saw its price crash 94% after insiders pocketed $250 million.
Prevention tips
- Thoroughly research the team behind any token before investing.
- Verify the developers' credentials and past projects.
- Examine the project's liquidity mechanisms.
- Ensure the code has been properly audited.
Pump and dump schemes
This type of scam thrives on FOMO (the fear of missing out) — a psychological trap that frequently ensnares crypto enthusiasts. Victims often worry they might miss out on a promising investment opportunity.
Scammers exploit this cognitive bias by artificially inflating a token's price through coordinated social media hype. This creates a false sense of demand, fueling investor interest and expectations of significant price rallies.
Once the price peaks, these criminals execute massive sell-offs, dumping their tokens on overly optimistic investors — who are ultimately left holding worthless assets. These exit strategies are typically carefully orchestrated.
Example
In 2022, Kim Kardashian agreed to pay $1.26 million in a settlement with the SEC over a 'pump and dump' scheme. The star had received $250,000 for promoting EthereumMax on her Instagram page — helping inflate the token's price before it was sold to investors. EMAX lost 99.8% of its value post-launch.

Prevention tips
- Educate yourself about common emotional biases in trading.
- Develop self-awareness of your own psychological tendencies.
- Base decisions on objective metrics like tokenomics.
- Never invest based solely on hype or social media trends.
How to protect yourself from crypto scams
Legitimate projects provide compelling and thorough documentation, team details, and other information before launch. Keep an eye out for signs of artificial hype and stay vigilant — here are the top 5 precautions.
- Use trusted platforms. Reputable crypto exchanges follow stringent security protocols including 2FA, providing multiple layers of cyber protection.
- Be wary of unsolicited offers. Unsolicited messages or emails promising spectacular returns with little to no effort should raise immediate red flags. Always double-check the legitimacy of these opportunities.
- Keep your private keys secure. Never share your private keys or wallet seed phrases with anyone — store them in a secure offline location, like a safe deposit box. Always double-check URLs to avoid phishing. For optimal security, keep most of your holdings offline in a hardware wallet.
- Stay informed. As scam methods constantly evolve, keep up with the latest crypto threats. Follow security news on trusted forums, cybersecurity sites, and educational resources. Subscribe to alertsfrom reputable sources like California's Department of Financial Protection & Innovation to stay updated.
- Verify ICOs and tokens. Thoroughly research any token, ICO, or DeFi project before investing. Price-tracking websites like CoinGecko and CoinMarketCap provide valuable data for verifying token details.
What to do if you fall victim to a crypto scam?
Consulting with a lawyer specializing in financial fraud is highly advisable. You may also contact a tax professional, as there could be tax implications for victims of crypto scams.
For US residents:
- File a report with the FBI's Internet Crime Complaint Center (IC3) or your local FBI field office
- Submit additional reports to:
- The Federal Trade Commission (FTC) at ReportFraud.ftc.gov
- The crypto exchange involved in the transaction
For EU residents:
- Consult the European e-Justice Portal for comprehensive information on victims' rights
- Report the incident to:
- Local police authorities
- National agencies like the National Crime Agency (NCA)
- The crypto exchange team
- Cybersecurity centers in your jurisdiction
If the fraud is large-scale or involves organized crime, consider reporting to the European Anti-Fraud Office (OLAF) or Europol's European Cybercrime Centre (EC3).
Wrapping up: Stay vigilant and informed
Crypto's explosive growth has created a gold rush for fraudsters, with scams evolving as quickly as the technology itself. From phishing to rug pulls, they target both newbies and seasoned investors. Each scam exploits different vulnerabilities, requiring equally nuanced defenses.
Navigate this space with relentless skepticism, education, and ironclad security habits. Verify everything and never let FOMO override common sense. Your greatest security vulnerability — and your strongest defense — is you.