Address poisoning scams: Don't copy-paste your fortune away

While pig butchering scams grab headlines, a sneakier threat is quietly targeting individual crypto holders. Using on-chain infrastructure and micro-transactions, criminals manipulate victims into making a single, costly mistake. Here's how address poisoning works and how to stay safe as 2026 rolls around.
What is address poisoning?
This attack vector leverages simple but highly effective logic: scammers forge an address that closely resembles the one you often use — and hope you’ll be sloppy enough to copy it.
- Surveillance. Scammers analyze your transaction patterns to detect your most frequently used addresses.
- Forgery. Using algorithms, they create a new address that closely mimics your trusted contact's — creating a deceptive lookalike.
- Poisoning. They send a minuscule, innocuous transaction from that fake address to your wallet. This "poisons" your transaction history.
- The trap. Later, if you hastily copy an address from your history, you might accidentally select the fraudulent one and send your assets directly to the scammer.
Scammers' poisoning arsenal
Scammers can buy address poisoning toolkits on the dark web (usually for cryptocurrency) and launch plug-and-play attacks with minimal hassle. Technical expertise is not a must — user-friendly interfaces make it easy for anyone to execute address poisoning. A kit typically features:
- Address generation software for creating lookalikes.
- Automated scripts for sending micro-transactions to targets.
- Detailed instructions on how to fool victims, tutorials, and even customer support via encrypted messaging platforms.
Here is a screenshot of a darknet forum whose user wanted to buy a tool to poison “several thousand addresses.”
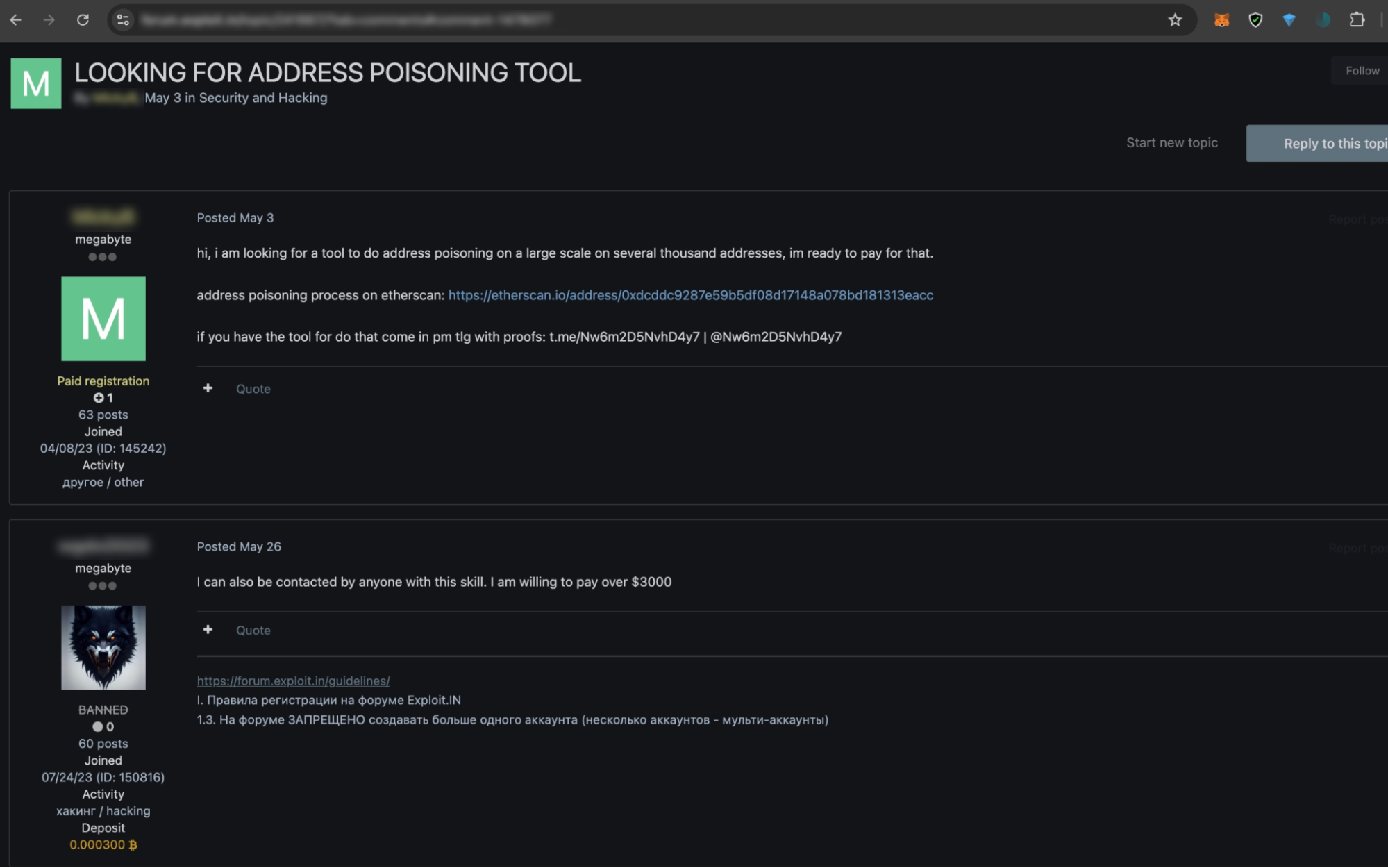
It is easy to see why address poisoning is increasingly widespread in the crypto space — the explosion of such toolkits has dramatically lowered the entry barrier for aspiring scammers.
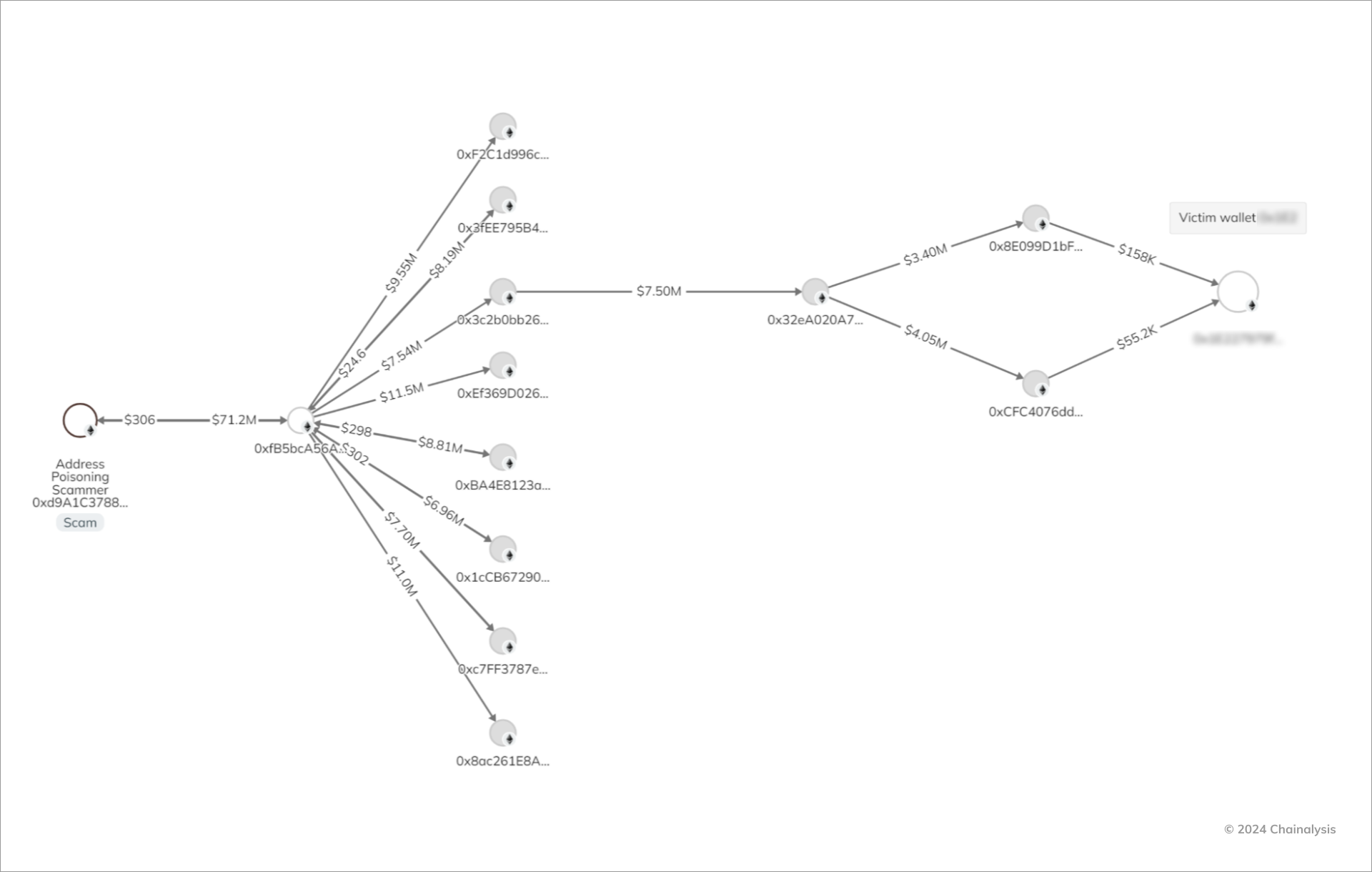
Example case: $68 million heist
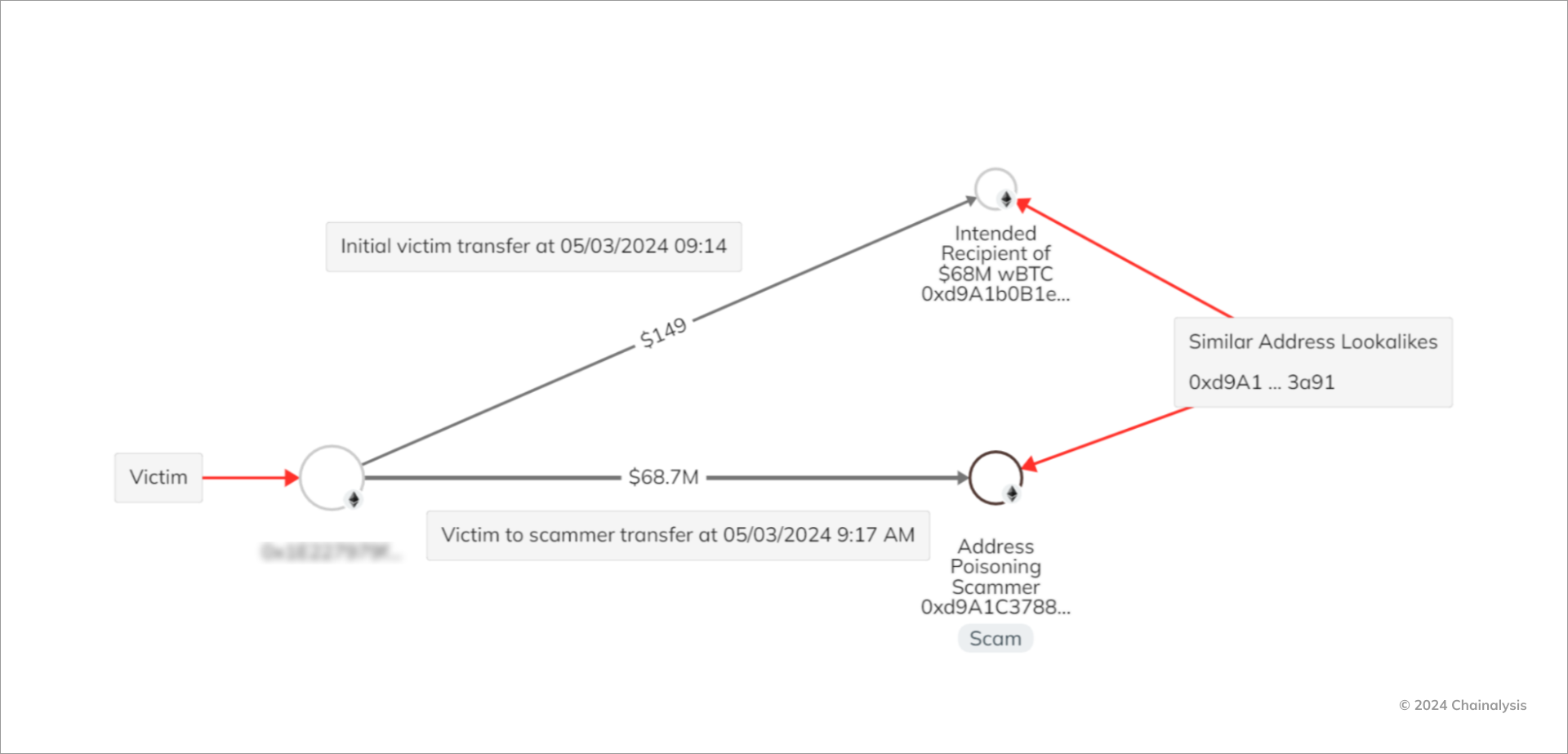
One of the biggest poisoning attacks to date took place on May 3, 2024, and nearly cost the victim $68 million in Wrapped Bitcoin (WBTC) before they managed to recover their funds. The whale's mistake was likely checking only the first and last few characters of the receiving address.
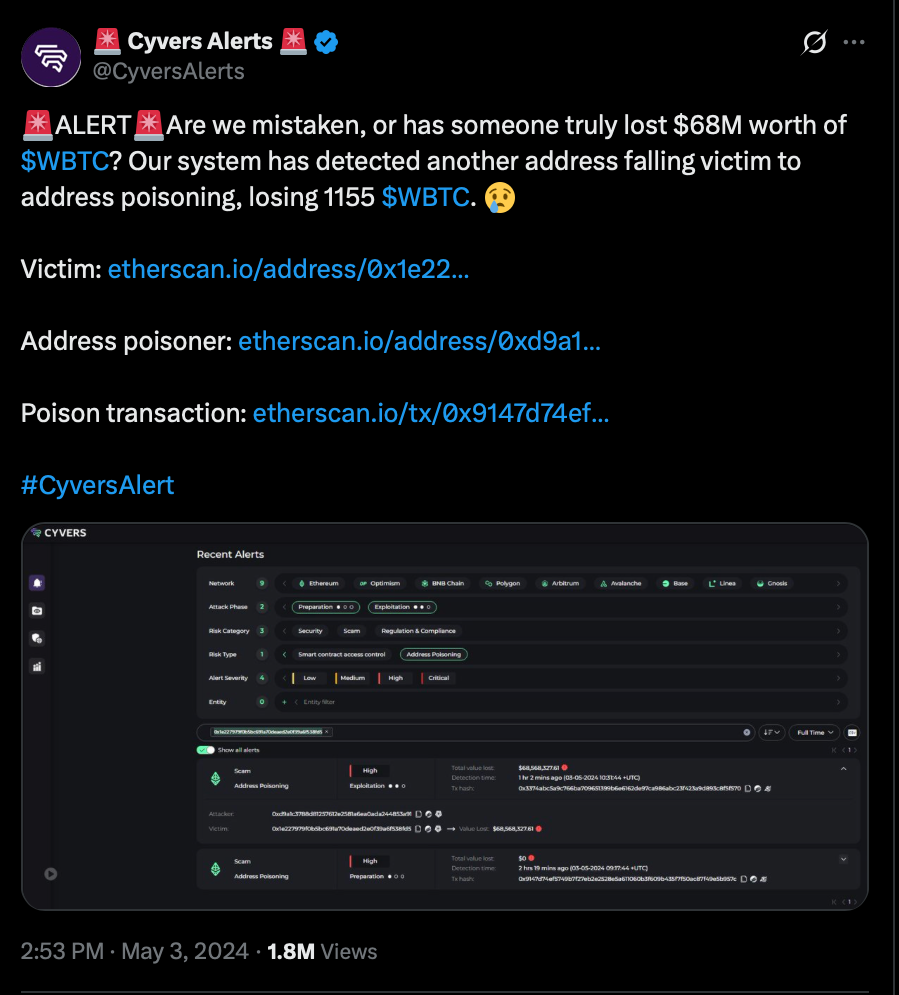
- The victim (0x1E227...) initially sent a transaction — probably a test payment — to a legitimate Ethereum address (0xd9A1b...). This is a standard safeguard before transferring significant amounts on-chain.
- Minutes later, they executed their planned large-scale transaction ($68 million in WBTC), confusing the recipient's address with the one controlled by the scammer (0xd9A1c...). That was an easy mistake to make, as the “0xd9A1” segments were identical.
- As WBTC appreciated within hours, the haul had grown to $71 million by the time the scammer moved it to another address.
- The victim communicated with the scammer via messages embedded in small ether (ETH) transactions, attempting to negotiate a return of the funds.
Six days after the attack (May 9), the scammer returned the original $68 million in ETH while pocketing $3 million due to price appreciation. The funds were sent back through multiple intermediary wallets. Chainalysis traced that path.
What helped the victim in this case was a strategic scare tactic. Here's one of their messages to the scammer:
“We both know there’s no way to clean these funds. You will be traced. We also both understand the ‘sleep well’ phrase wasn’t about your moral and ethical qualities.”
Role of “seeder” wallets
This attack campaign involved the use of 8 “seeder” wallets. Each created additional seeder wallets and over 82,000 “seeded wallets” — addresses mimicking those of legitimate recipients. Chainalysis found that 2,774 victim wallets sent funds (a total of $69,720,993) to those malicious addresses.
The number of seeded addresses accounted for just under 1% of all new Ethereum addresses generated while the campaign was running. However, this estimate is tentative and may underrepresent the actual scale of the attack.
How successful was this campaign?
The $68 million theft was a rare success — a measly 0.03% of all malicious addresses received over $100 from targets. This estimate excludes transfers from the scammers themselves.
By Chainalysis estimates, the scammers netted $1.49 million, with a return on investment (ROI) of 1,147.62% (12.47 times the cost). For comparison, the typical scam campaign that year made a median amount of roughly $400.
However, had the scammers not returned the $68 million, their ROI could have soared to 58,363% (584 times the initial amount).
How do scammers identify targets?
Naturally, address poisoning typically hunts large balances, which also suggests the victims are more experienced than the average user. They are more active and have a longer on-chain footprint.
In the case mentioned above, the victims had balances above $338,900, with a median balance near $1,000,000. Their addresses were roughly 512 days old and had conducted 598 transfers on average.
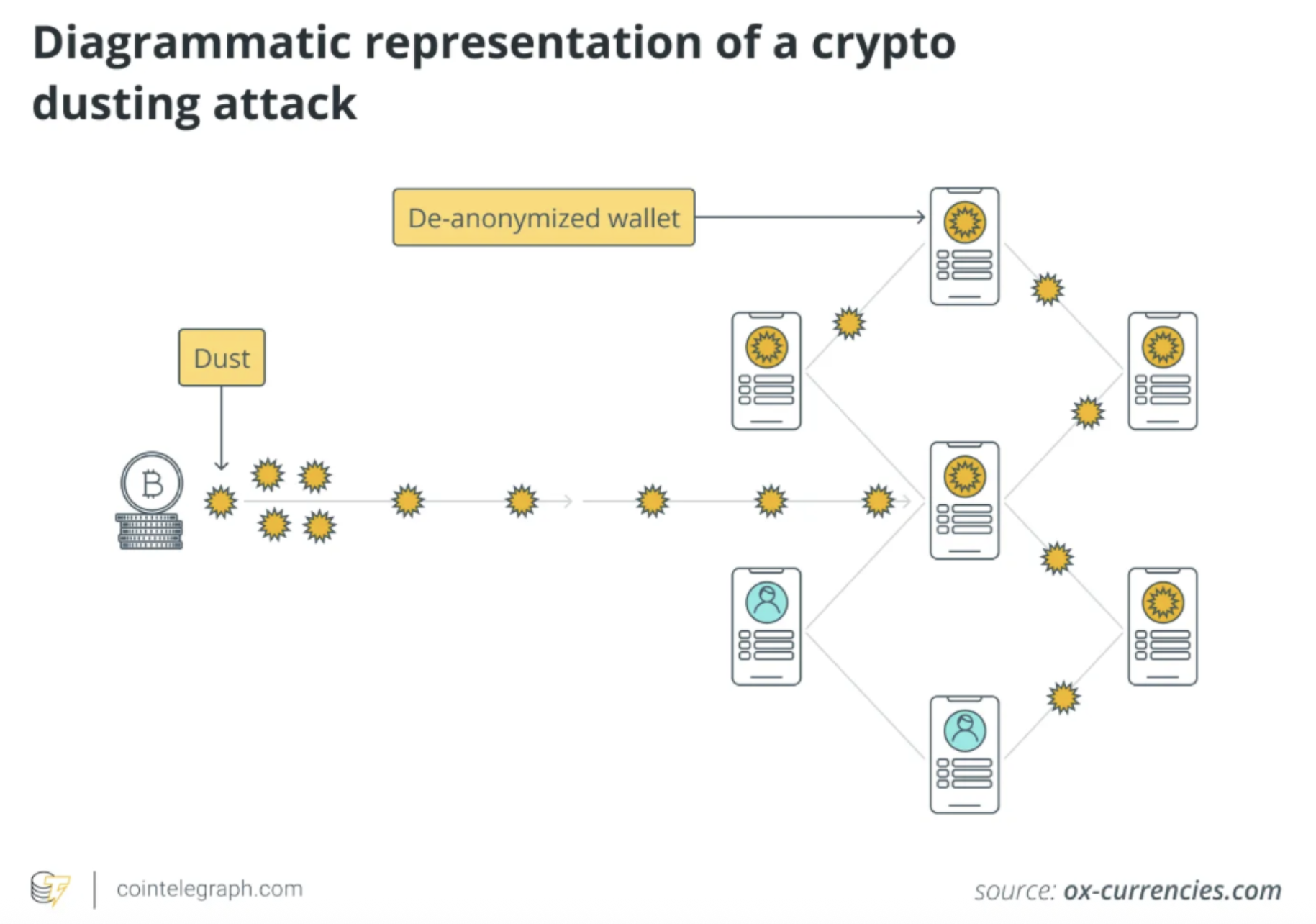
Address poisoning vs. dusting attacks
Address poisoning should not be confused with dusting, another method of on-chain deception. Dusting attacks also involve sending negligible amounts of crypto to a target's wallet, but the goals sharply diverge.
Address poisoning victims send their own funds to a fraudulent mimic; a dusting attack aims to unmask the recipient by watching how the "dust" is spent. By linking wallets to one another, scammers can piece together a real-world identity to conduct blackmail, extortion, or sophisticated phishing campaigns.
In essence, dusting is an attack on your privacy and a prelude to future targeting, while address poisoning is a direct attack on your assets, banking on a single moment of confusion. Recognizing this difference is the first step in deploying the right defenses for each distinct threat. Learn more in our full guide to dusting attacks.
Protect yourself from address poisoning
Don’t let scammers catch you off guard. Arming yourself with knowledge and disciplined habits is your best defense. Here’s how to protect your assets:
- Watch for tiny transactions. Small, mysterious deposits from unknown addresses are a major red flag. Scrutinize your transaction history regularly — these are the "seeds" of a poisoning attempt.
- Verify every address, completely. Before sending any crypto, meticulously check the fulladdress — don’t just skim the first and last few characters. Use QR codes from trusted, original sources whenever possible.
- Leverage your address book. Use your wallet’s built-in address book (a feature in apps like MetaMask) to securely store and label frequent contacts. This creates a trusted shortcut and drastically cuts the risk of selecting a counterfeit address from your history.
- Avoid the copy-paste trap. Be wary of copying addresses directly from your transaction history — sophisticated malware can even swap them on your clipboard. For any significant transfer, confirm the address directly with the recipient through a separate, verified channel.
- Upgrade your security posture. Keep your wallet software updated and consider a hardware wallet for storing large sums. Always send a small test transaction first before moving a major amount.
What to do if you become a victim
If you suspect you’ve fallen for an address poisoning scam, act fast. The following steps won’t guarantee recovery, but they represent your strongest chance to limit or eliminate the damage.
#1 Report to your platform ASAP
If you’re using a licensed crypto platform, notify their support team at once. While they may not be able to reverse transactions, this formal report is a vital first step for any legal or investigative follow-up.
#2 File a formal police report
Platforms typically require official orders to act. Secure a police report — this document carries necessary legal weight.
#3 Pursue stablecoin recovery (e.g., USDT)
If stolen funds involve assets like Tether (USDT), there is a possible, though complex, path. Issuers can sometimes freeze addresses or, in rare cases, facilitate recovery. This process is highly technical, lengthy, and requires expert legal guidance.
#4 Meticulously gather all evidence
Save everything — transaction IDs (TXIDs), blockchain explorer links, screenshots, and all communications. This evidence is your essential ammunition for any recovery effort or legal action.
Wrapping up
Address poisoning is a silent, algorithmic threat that turns a moment of routine carelessness into a devastating financial loss. Its insidious power lies not in technical brilliance, but in exploiting the most predictable element in crypto: human oversight.
Experience and large balances make you a prime target, not a shielded one. The true victory is in prevention, so make vigilance your non-negotiable habit. Use address books religiously, verify every single character, and treat your transaction history with healthy suspicion. While the steps for recourse exist, recovery is an arduous, uncertain battle.