What is Q-Day? Quantum threat to Bitcoin explained
As quantum computing leaps forward, chatter about its potential threat to crypto is reaching a fever pitch. The current tech is too unstable to breach real-world cryptography — but the walls protecting Bitcoin could eventually be shattered. Should you be worried?
What is the “Q-Day” threat?
Quantum computers leverage the bizarre principles of quantum mechanics to crunch data way faster than regular computers. They challenge our understanding of how the world works.
While everyday machines use simple binary bits (0s or 1s), these rivals use quantum bits, or qubits. These subatomic particles can exist in multiple states at once and influence each other in an instant, even across distances, thanks to weird phenomena like superposition and entanglement.
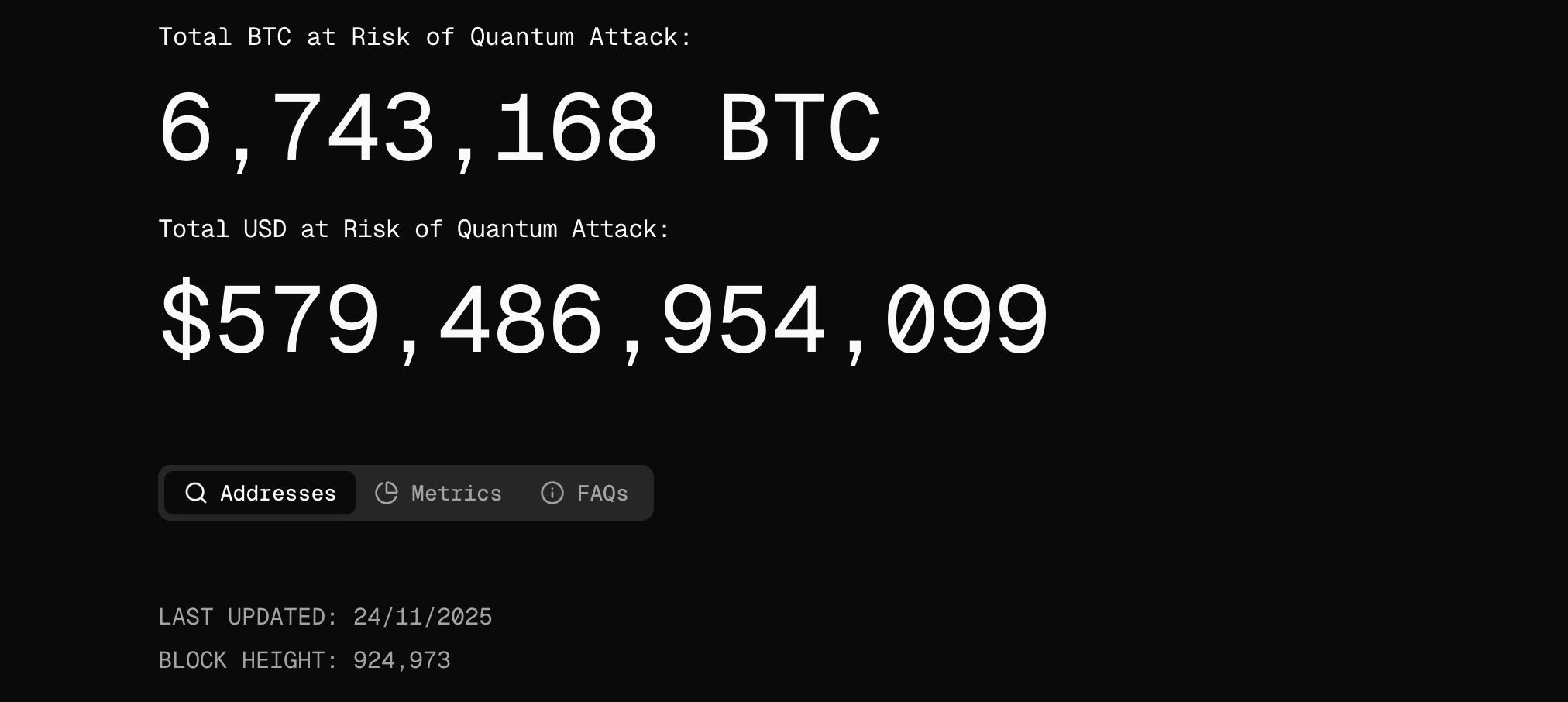
Experts fear that quantum computers may one day crack the digital signatures guarding our assets — forging signatures to drain wallets and putting over $579 billion at risk. Given the recent progress from IBM and Google, this “Q-Day” may creep up on us faster than we think.
The term “Q-Day” paints a picture of the hypothetical moment a mighty, fault-tolerant quantum system breaks into older Bitcoin addresses. Armoring the blockchain against this quantum threat will take years, which means we need to start building our defenses now.
The tricky part is — nobody knows when Q-Day will dawn or how to get ready.
Inside a quantum attack
In theory, hackers armed with quantum power could reverse-engineer the private keys to Bitcoin wallets. This assault would use Shor's algorithm to crack Bitcoin’s elliptic-curve signatures, which get their strength from the immense difficulty of the discrete logarithm problem.
Pioneered by mathematician Peter Shor in 1994, this method would unlock the ability for quantum computers to factor large numbers with staggering efficiency, running circles around any classical machine.
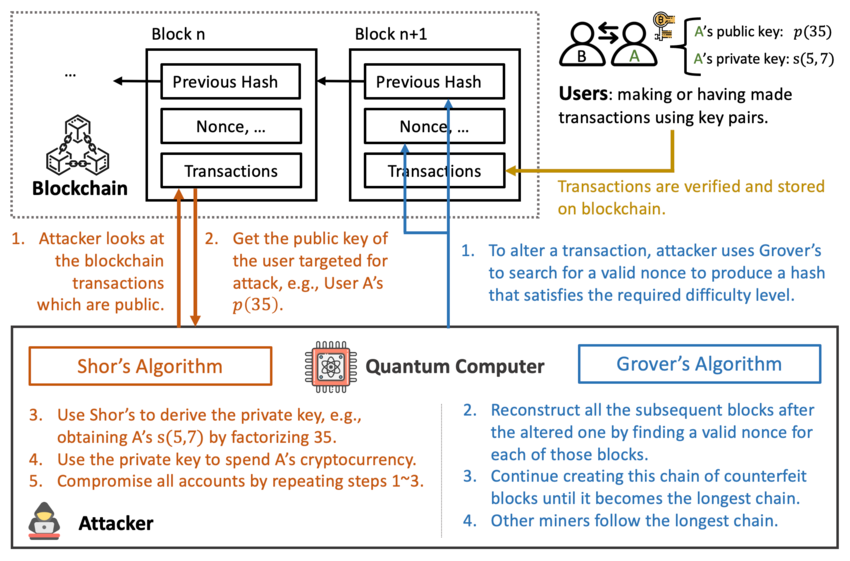
Here's how this scenario could play out:
- Hunting for addresses with exposed public keys (e.g., dusty old wallets, early miner rewards, and long-forgotten accounts).
- Snatching those keys and feeding them through a quantum computer using Shor’s algorithm to unlock the private keys.
- Making off with the coins.
With an army of error-corrected qubits, a quantum computer could pull it off. It would forge Bitcoin's digital signature to authorize a raid on the victims’ accounts.
That signature would look completely authentic on-chain — nodes would be none the wiser, and miners would rubber-stamp it into a block. Panic would sweep through the markets before anyone realized that a quantum attack was underway.
Imagine countless addresses being emptied all at once. A flood of billions of dollars vanishing in the blink of an eye.
Pulling off these incredibly complex calculations would require physical qubits to have sufficiently low error rates to form reliable logical qubits. The latter must then entangle — forge a deep connection — locking into a shared quantum state, even when far apart. The particles must also perform millions of logical operations without a single misstep.
State of quantum computing in 2025
So, how close are we to this scenario becoming real? The current buzz around quantum computing is understandable — this technology has burst out of science fiction and into the lab.
In 2024, Microsoft and Atom Computing stunned the industry by unveiling a commercial quantum machine with the largest number of entangled logical qubits ever achieved. In 2025, the pace of innovation has been relentless, with major leaps nearly every month:
- In January, Google’s 105-qubit Willow chip showed a dramatic error reduction; in just five minutes, it blitzed through calculations that would grind traditional supercomputers for an impractical amount of time.
- In February, Microsoft unveiled Majorana 1, the world’s first quantum chip powered by its Topological Core architecture, setting a new record for logical-qubit entanglement with Atom Computing.
- In April, the National Institute of Standards and Technology (NIST), teaming up with other researchers, extended superconducting qubit coherence to 0.6 milliseconds.
- In June, IBM kicked off a project to build the world’s first fault-tolerant quantum computer, setting its sights on 200 logical qubits by 2029 and over 1,000 in the early 2030s.
- In October, Google’s Willow processor notched a verified quantum speed-up, while IBM succeeded in entangling 120 qubits.
- In November, IBM unveiled its Nighthawk and Loon quantum processors, chips designed to achieve community-verified quantum advantage by 2026 and fault-tolerance by 2029.
Cracks in Bitcoin's armor
At its core, Bitcoin’s security relies on a kind of mathematical magic known as elliptic-curve cryptography. But this system has a subtle flaw: the moment you spend from a Bitcoin address, you broadcast its public key to the entire network — and that exposure is etched into the blockchain forever.
The earliest "pay-to-public-key" addresses were the most careless, revealing their public keys right from the start. Later "pay-to-public-key-hash" formats were more cautious, keeping the key under wraps until the first time the coins were spent.
This means the oldest coins in existence, including the legendary ~1 million Bitcoin from the Satoshi era, are sitting ducks. Their public keys are already out in the open, waiting for a future quantum computer to unlock them.
Switching to post-quantum digital signatures is not automatic. Justin Thaler, research partner at Andreessen Horowitz and associate professor at Georgetown University, explained:
“For Satoshi to protect their coins, they’d have to wake up and move them into new post-quantum-secure wallets. The biggest concern is the forgotten fortune — about $180 billion in abandoned coins, including roughly $100 billion thought to belong to Satoshi himself. That’s a massive prize, but it's frozen in time, and that’s the real danger.”
What makes the problem worse is coins tied to lost private keys. Many have been gathering digital dust for over a decade. Without those keys, they can never be evacuated to safety, making them perfect, permanent targets.
No one can magically freeze Bitcoin on the blockchain, so our only practical defense is to actively shepherd vulnerable funds into new, quantum-resistant addresses. However, this new armor comes with a hefty price tag.
Post-quantum encryption is a bulky replacement for today's sleek 64-byte signatures. These versions could be 10 to 100 times larger — a major data burden, given that every single node must store every signature forever.
Building Bitcoin's quantum fortress
So, how do we reinforce the walls? Developers have formulated several Bitcoin Improvement Proposals (BIPs), each taking a different path to protection.
#1 Hybrid shield: BIP-360 (P2QRH)
This creates new “bc1r…” addresses that pair today’s elliptic-curve signatures with a post-quantum bodyguard. It’s a defensive upgrade that doesn’t require a network split, but the bulkier signatures mean higher transaction fees.
#2 Sleeper agent: Quantum-safe Taproot
This adds a hidden, post-quantum branch to existing Taproot addresses. The network sprints into action only if a quantum threat emerges, requiring miners to activate the new defenses via a soft fork.
#3 Great migration: QRAMP
This is a more radical plan — a likely hard fork that would force-move all vulnerable coins into quantum-safe addresses.
#4 Quick fix: Pay to Taproot Hash (P2TRH)
This cleverly rejigs Taproot to dramatically reduce the window of exposure without breaking compatibility or needing new math.
#5 Compression wizard: Non-Interactive Transaction Compression (NTC) via STARKs
This uses mind-bending zero-knowledge proofs to squeeze a block full of giant post-quantum signatures into a single, tiny proof, slashing storage and fee costs.
Other creative ideas are also on the table, like "commit-reveal" schemes that rely on publishing coded commitments in advance, or "poison pill" transactions that let users pre-program a recovery path.
Taken together, these blueprints chart a course: start with low-impact fixes like P2TRH now, and deploy the heavier artillery like BIP-360 or STARK compression as the quantum threat looms larger.
Bitcoin’s greatest strength is its biggest weakness
Any new signature scheme requires consensus across miners, developers, and users. Not only does decentralization make monumental upgrades slow and grueling — the owners of abandoned coins are also long gone. The community may simply have to burn those assets to keep quantum-equipped attackers at bay.
What should you do?
For now, don’t panic. A few smart habits go a long way in shrinking your long-term risk:
- Never reuse addresses. This keeps your public key hidden until the moment you spend.
- Stick with modern wallet formats like SegWit and Taproot.
The reality is, today’s quantum computers are still playing in the minor leagues; they aren’t close to threatening Bitcoin. Predictions for "Q-Day" are all over the map — some researchers see a threat in the next five years, while others push it into the 2030s.
But with billions pouring into quantum research, the timeline could accelerate in a flash. The clock is ticking, and the race to future-proof Bitcoin is officially on.